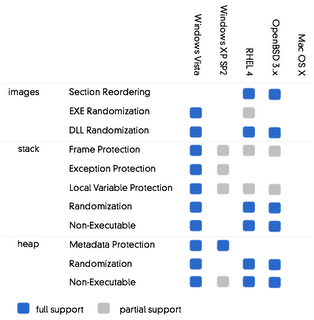
The chart shown compares security measures in-built into various operating systems. Blue is great, gray is good, white is bad. The operating systems are listed across the top; the security measures being assessed are down the side. These are all measures which have made their way from academic think-tanks into real-world code only during the last few years. More details here. Windows as the most widely used of the operating systems out there, has been the biggest target for hackers, and therefore OS X or RedHat LInux may be less of a threat in some sense. And to be fair, the chart is a bit behind on the features offered by OS X, which will undoubtedly improve in the next release. Still, the chart clearly shows that anybody with the hardware to upgrade to Vista from XP should do so quam primum.
3 comments:
MHA, I'm not sure how much you want to take from that chart as evidence of Vista's superiority over other operating systems; I'll agree that it argues forcefully that Vista should be more secure than previous versions of Windows. But a number of those security features are fixes for architectural weaknesses that are part of Windows history. I'm not real up on Vista internals, but just looking at them, an awful lot of them are fixes for problems that don't exist in modern UNIX variants, like Solaris and Darwin (Mach, OS/X). So, for example, the first five entries in the list aren't necessary in a modern UNIX because the whole executable lives in a seperate virtual address space, protected by hardware memory mapping; links to shared executables are done in the creation of the memory map, and don't have a known vector table to exploit. Random mallocators are available, but since the kernel doesn't live in the same address space, all a misuse of a malloc pointer can do is use your own program to expire with a segmentation violation; stack protection with randomization is useful in some cases, but code injection attacks are actually pretty rare against a UNIX operating system, if not against some application code (like web servers.)
All in all, it seems to mostly come down to "we have all the best, most technically advanced leak plugging and bailing mechanisms" ... the advantages of which are pretty academic if your boat doesn't leak to start with.
Note that RHEL 4 is about two years old and RHEL 5 should be out this summer.
When I upgrade my machine this summer I might run virtualized XP just to have access to some of the business standard stuff like PPT so I can do more work at home. But even if I could figure out which Vista package to get I doubt I will spend the big bucks. My needs really aren't all that much -- browsing, editing, compiling -- and Linux fills them out of the box and doesn't cost a penny. Not to mention that Linux still does the networking thing better. SSH, CVS, SVN, Python, /dev/random, and all that good Unixy stuff takes actual work to get up on windows. And what the heck is that \r\n crap for line endings? The teletype age ended with hobbyist machines back in the 70's. At least Apple came to it's senses. And don't get me started on binary files vs text files. Why, I ask, why? Anyway, I suspect Vista just ain't worth the trouble.
Question: is Vista a multiuser system? And I mean multiuser in that lots of folks can log in and run at the same time. A single license really ought to support this. It's called networking.
That said, having a working shell on Vista with a new scripting language sounds great, I love the command line. But it is all a bit late.
PS, Seneca, a lot of those things are to avoid buffer overflows on the stack. This is a problem with old hardware with executable stack memory and C coding practices. Memory mapping and controlling r/w/x access to the text/data/bss parts of an executable doesn't help with that.
My Macs just work. When they stop working, maybe I'll pay attention. I spend 0 time (that's a ZERO) thinking about my operating system and I'd like to keep it that way.
Post a Comment